Common Cloud Models
220-1101: Objective 4.1: Summarize cloud-computing concepts.

The cloud refers to any type of computing—including program execution, storage, or services—that takes place remotely. Understanding basic cloud concepts is important for technicians, who will increasingly be asked to manage software or data in the cloud. Some of those functions are described in the following sections.
IaaS
Infrastructure as a Service (IaaS) enables customers to purchase access to data center infrastructure such as storage, network, and networking services. In this model, the cloud provider covers the costs and work involved in equipment, firewall configurations, and other maintenance. Thousands of companies are realizing that they can reduce the costs of their network infrastructure by outsourcing storage and computing services to a cloud provider. These include new startup companies that lack the capital resources to buy and manage equipment as they grow and established companies that want to reduce the costs related to backup and storage of their networks.
One key feature of IaaS is the flexibility it offers to customers, who can now just use the virtual resources they need when they need them instead of having to pay for them when they don’t need them.
IaaS puts users in charge of all the software used in a project, from applications and data to the operating system. IaaS vendors supply the hardware and network support tools.
Amazon first introduced cloud services in 2006, and the field of cloud providers continues to grow. At press time, the three largest cloud providers are as follows:
Amazon Web Services (AWS)
Microsoft Azure
Google Cloud
SaaS
Software as a Service (SaaS) refers to software that is hosted on servers and accessed through a web browser. Because SaaS processing is performed at the server, a thin client, smartphone, or tablet is sufficient to run the software. A browser-based service that does not require a user to download an application code to use the service is an example of SaaS.
Perhaps the best-known SaaS is Google Mail (Gmail). Gmail servers provide the Gmail service to anyone who has a web browser. Other examples of SaaS include the following:
Google Docs: Word processing, spreadsheets, presentations, and forms (www.google.com/intl/en/docs/about/)
Microsoft Office 365: Word processing, spreadsheets, presentations, calendar, collaboration, and email (www.office.com)
FreshBooks: Small business accounting (www.freshbooks.com)
Salesforce: Customer relationship management (www.salesforce.com)
Basecamp: Project management (https://basecamp.com)
SaaS is a cloud-based software licensing and delivery model that grants customers access to software on a subscription basis using the SaaS vendor’s servers. SaaS is designed for organizations that need to use a service rather than develop or deploy one. Figure 4-2 illustrates the word processor in Google Docs.
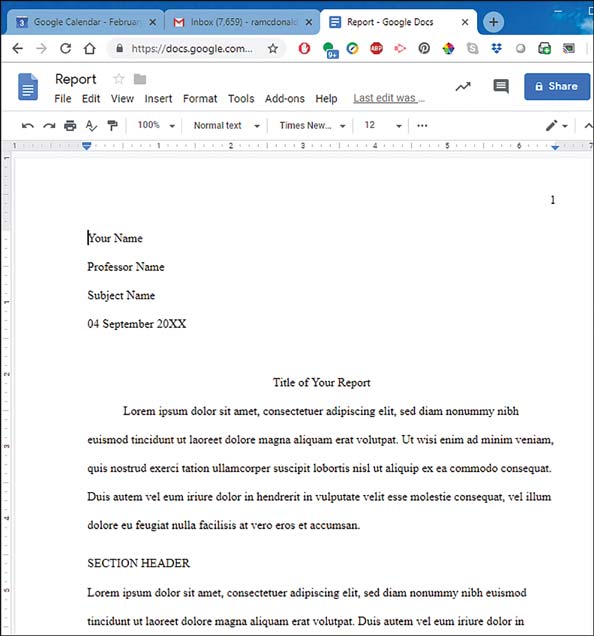
Figure 4.2 Using the Google Docs Word Processor to Create a Report from a Template, with Random Text as Placeholders
PaaS
Platform as a Service (PaaS) enables vendors to develop and deploy application software in a cloud environment. A developer using PaaS can concentrate on software features instead of possible issues with server hardware and operating systems.
Some of the major PaaS vendors include the following:
Oracle Cloud: https://cloud.oracle.com
Google Cloud Platform: https://cloud.google.com
Microsoft Azure: https://azure.microsoft.com
Salesforce Platform: www.salesforce.com
Many vendors provide many services across multiple platforms.
Keep in mind the following considerations in selecting a PaaS vendor:
Language and server-side support: Make sure the vendor selected supports the languages used for development and the server-side technologies the apps depend on. Most major PaaS vendors support languages such as Java, Ruby, PHP, and Python, but server-side technology support varies a great deal.
Integration with existing investments: Some PaaS vendor products can integrate with existing apps and data, meaning that cloud platforms can work with existing resources instead of requiring users to replace them entirely.
Costs: Most PaaS vendors use pricing by the hour, but some price by the month. Be sure your precommitment cost estimations take into account the software tools and services you need; pricing can vary according to the tools or services bundled.
Public vs. Private vs. Hybrid vs. Community
Four general types of cloud computing are used. Each type can have variables in its implementation, depending on customer needs.
Public cloud computing is available to any organization that signs up or pays for it. The connection between services and organizations is the public Internet. Public cloud computing typically includes built-in features and tools that would be too expensive to implement on their own. This allows organizations to pay for the features and options needed without buying, setting up, and maintaining the hardware themselves.
Private cloud computing is available only to authorized users in divisions or departments of a single company. The company owns and manages the cloud behind its corporate firewall, and its employees maintain the equipment. Private cloud computing is considered to be more secure than public cloud computing. Private cloud computing is great for organizations that are highly regulated or need strict control over business-critical data, such as financial or health care organizations.
Hybrid cloud computing combines features of public and private cloud computing. A typical hybrid installation includes dedicated and cloud-based servers and high-speed interconnections with load balancing to move workloads between the environments as needed. Hybrid cloud computing is best for organizations that need to utilize both private and public clouds. For example, a financial institution might want to store critical and sensitive data on a private cloud while using a public cloud to store lower-risk data.
Community cloud computing is a type of hybrid cloud computing used by different organizations that are working together. The organizations work as partners to build the community cloud and share its costs. This model works well for organizations that are working together temporarily on a single goal or project. When the project is finished, they can dissolve the cloud.
Cloud Characteristics
Cloud computing is a generic term that can encompass several different computer network models and features that serve a customer’s unique requirements. This section describes different ways a computer cloud can be designed and implemented to meet the computing and network needs of a company or institution.
Shared Resources
Shared resources refers to the practice of sharing equipment or data on a network to save costs. This is the most common reason for implementing cloud computing. The way clouds are designed and implemented can vary according to the customer’s needs. Devices and data can be shared over the Internet in two main ways: using an internal cloud or using an external cloud.
Internal Cloud
Internal and external clouds are defined by the ownership of the cloud’s resources. With an internal cloud, a company might need the flexibility of cloud services but also have security and guaranteed availability requirements that prevent the company from accessing cloud services outside its own network. An internal cloud is similar to a private cloud, but it is built and owned inside the organization. With an internal cloud, the company gets the virtualization services and flexibility of a commercial cloud, but with the security and reliability that comes from existing within the company’s network infrastructure. The cost of an internal cloud might be higher than the cost of outsourcing to commercial services, but sharing resources internally still reduces the cost.
External Cloud
An external cloud is a cloud solution that exists outside an organization’s physical boundaries. It can be private, public, or community based, as long as it is not located on an organization’s property.
Rapid Elasticity
Rapid elasticity refers to the capability to rapidly scale up and scale back cloud computing resources as needed. For example, selling high-demand concert tickets in the days before cloud computing often resulted in crashing servers and disappointed customers. Thanks to the rapid elasticity of the cloud, high-demand events can quickly expand capacity for online sales without leaving customers unserved when they try to buy.
High Availability
The cloud is always up and open for work. Providers maintain reliable service by replicating cloud servers in clusters within their data centers. This way, if one server crashes, other servers can pick up the work.
Another way providers ensure reliable high availability is to replicate entire data centers in different parts of a geographical region, or even across the globe. This model ensures that a customer’s computing services will not be disrupted by natural disasters such as earthquakes, fires, and storms. With global availability, customers can place their services closest to their customers around the world, to reduce access time to web servers and data.
File Synchronization
Storing, moving, backing up, and updating data can be a huge task for a company’s IT department. Cloud providers have designed file synchronization services to make replicating on-premises data synching to multiple sites both automated and reliable. AWS DataSync and Microsoft’s SQL Data Sync are two examples of this specialized service. These automated services allow companies’ IT departments to focus on other tasks.
On-Demand
On-demand is a shortened term for on-demand self-services. On-demand self-services from SaaS providers such as Salesforce.com, Gmail, and others are available to customers when they need them but do not need to be maintained by the customer when they are not needed.
Metered Utilization
Organizations purchase cloud computing services in much the same way as utilities such as gas, water, and electricity. With metered utilization, these services are measured in some way, and the price is based on the amount used. Cloud providers can base prices in different ways for different services. For example, cloud computing services are metered by the minute: The user pays only for the minutes used. Storage services are usually charged by the gigabyte. More complex cloud services, such as replication of servers to be used in different areas, charge by the instance of snapshots or other services.
Of course, cloud providers have many different pricing schedules. Three common ones follow:
Pay as you go: The customer pays only for services used and pays for computing time only when needed. This can be beneficial for new businesses that are unsure of their future computing needs.
Bulk purchasing: This arrangement is similar to pay-as-you-go pricing, but it involves a commitment to use a specific amount over a period of one to three years.
Tiered pricing: The more services are used, the less they cost per unit. For example, the more storage service a company purchases, the less it pays per gigabyte of storage.
Metered cloud services can mean immense savings for customers whose computing needs are periodic or uncertain, and their popularity accounts for much of the growth of cloud services. To save money, many companies are outsourcing their data center tasks to the cloud.
Desktop Virtualization
Desktop virtualization refers to creating a user interface to a computer that is hosted on a central server on-premises or perhaps in the cloud. Either way, the user experience with the virtual desktop is the same. When a company uses a vendor’s virtual desktop infrastructure (VDI), users can use minimally powered devices with an Internet connection and work as if processing were happening locally. Basically, VDI allows organizations to offer users remote access to virtual desktop environments from almost any device, such as a smart phone, tablet, or laptop. They can access this through client software installed on their local device or on a web browser.
Desktop virtualization is also known as thin client networking because the processing is centralized. Only mouse and keyboard inputs are sent across the local network for on-premises VDI or across the Internet for VDI in the cloud.
When a VM has an operating system installed, it appears and can behave like any other computer on a network. To interact with other machines, it needs to have a virtual network interface card (NIC) installed so that it can have a physical MAC address and an IP address. The virtual NIC behaves almost exactly like a physical NIC, but the administrator can use the virtual machine manager (VMM) to assign a specific MAC address. This is different from physical NICs with MAC addresses that are burned into the hardware by the manufacturer.
If administrators want the VM to communicate with other machines, they can create a path, or bridge, between the virtual NIC and the physical NIC on the VMM hardware. This allows the VM to communicate like any other machine in the LAN. In Hyper-V, this can be done by creating a virtual switch under the Virtual Switch Manager (see Figure 4-3).
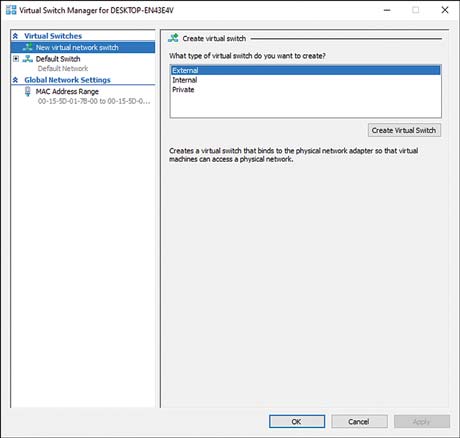
Figure 4.3 Creating a Virtual Switch in Hyper-V
