Footprinting
Footprinting is the first step of the hacking methodology, and it is all about gathering information. Most organizations share a tremendous amount of information and data through various channels, including their websites and social media pages, their employees, and even their help desks. Footprinting is about information gathering and is both passive and active. Reviewing the company’s website is an example of passive footprinting, whereas the act of calling the help desk and attempting to social engineer them out of privileged information is an example of active information gathering. Port scanning entails determining network ranges and looking for open ports on individual systems. The EC-Council divides footprinting and scanning into seven basic steps, as illustrated in Figure 3-1.

Figure 3-1 Footprinting and Scanning Steps
Many times, students ask for a step-by-step method of information gathering. Realize that these are just generic steps and that ethical hacking is really the process of discovery. Although the material in this book is covered in an ordered approach, real life sometimes varies. When performing these activities, you might find that you are led in a different direction from what you originally envisioned.
Footprinting Methodology
The information-gathering steps of footprinting and scanning are of utmost importance. Reconnaissance can be active or passive. Active means that you (the pen tester or ethical hacker) are using tools such as scanners to gather information about your targeted system. In other words, you are “actively” sending IP packets and interacting with the targeted system or network. In passive reconnaissance, you do not send any IP packets or interact with your target, but instead leverage publicly available information. This information is also known as open source intelligence (OSINT).
Table 3-2 MITRE ATT&CK Reconnaissance Techniques and Subtechniques
Technique |
Subtechnique |
|---|---|
Active Scanning |
Scanning IP Blocks Vulnerability Scanning |
Gather Victim Host Information |
Client Configurations Firmware Hardware Software |
Gather Victim Identity Information |
Credentials Email Addresses Employee Names |
Gather Victim Network Information |
DNS Domain Properties IP Addresses Network Security Appliances Network Topology Network Trust Dependencies |
Gather Victim Org Information |
Business Relationships Determine Physical Locations Identify Business Tempo Identify Roles |
Phishing for Information |
Spearphishing Attachment Spearphishing Link Spearphishing Service |
Search Closed Sources |
Purchase Technical Data Threat Intel Vendors |
Search Open Technical Databases |
CDNs Digital Certificates DNS/Passive DNS Scan Databases WHOIS |
Search Open Websites/Domains |
Search Engines Social Media |
Search Victim-Owned Websites |
Good information gathering can make the difference between a successful pen test and one that has failed to provide maximum benefit to the client. This information can be found on the organization’s website, published trade papers, Usenet, financial databases, or even from disgruntled employees. Some potential sources are discussed, but first let’s review documentation.
Documentation
One important aspect of information gathering is documentation. Most people don’t like paperwork, but it’s a requirement that you cannot ignore. The best way to get off to a good start is to develop a systematic method to profile a target and record the results. Create a matrix with fields to record domain name, IP address, DNS servers, employee information, email addresses, IP address range, open ports, and banner details. Figure 3-2 gives an example of what your information matrix might look like when you start the documentation process. You can use simple tables, notes, or mind maps like the one illustrated in Figure 3-2.
Building this type of information early on will help in mapping the network and planning the best method of attack.
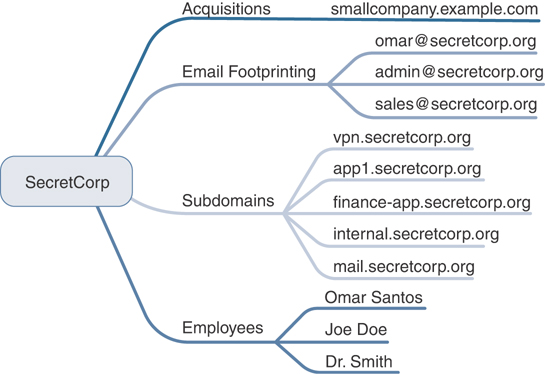
Figure 3-2 Documentation Finding
Footprinting Through Search Engines
Most people use Google, DuckDuckGo, or other search engines to locate information on the Internet. What you might not know is that search engines, such as Google, can perform much more powerful searches than most people ever dream of. Not only can Google translate documents, perform news searches, and do image searches, but it also can be used by hackers and attackers to do something that has been termed Google hacking.
Through the use of basic search techniques combined with advanced operators, Google can become a powerful vulnerability search tool. Table 3-3 describes some advanced operators.
Table 3-3 Google Search Terms
Operator |
Description |
|---|---|
Filetype |
Directs Google to search only within the text of a particular type of file. Example: filetype:xls |
Inurl |
Directs Google to search only within the specified URL of a document. Example: inurl:search-text |
Link |
Directs Google to search within hyperlinks for a specific term. Example: link: www.domain.com |
Intitle |
Directs Google to search for a term within the title of a document. Example intitle: “Index of.etc” |
Through the use of the advanced operators shown in Table 3-3 in combination with key terms, Google can be used to uncover many pieces of sensitive information that shouldn’t be revealed. A term even exists for the people who blindly post this information on the Internet; they are called Google dorks. To see how this works, enter the following phrase into Google:
intext:JSESSIONID OR intext:PHPSESSID inurl:access.log ext:log
This query searches in a URL for the session IDs that could be used to potentially impersonate users. The search found more than 100 sites that store sensitive session IDs in logs that were publicly accessible. If these IDs have not timed out, they could be used to gain access to restricted resources. You can use advanced operators to search for many types of data. Figure 3-3 shows a search where Social Security numbers (SSNs) were queried. Although this type of information should not be listed on the web, it might have been placed there inadvertently or by someone who did not understand the security implications.
Finally, don’t forget that finding a vulnerability using Google is not unethical, but using that vulnerability can be unethical unless you have written permission from the domain owner. For example, here is a link to the Google hack for Shellshock (a Bash vulnerability introduced later in the chapter): https://www.exploit-db.com/exploits/34895/. Notice how it took only a few minutes for an attacker to gather this type of information. Security professionals should always be concerned about what kind of information is posted on the web and who can access it.
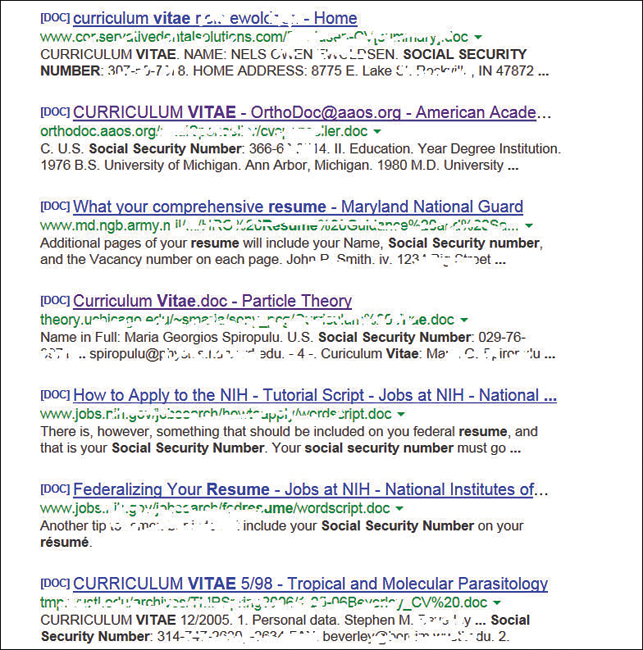
Figure 3-3 Google Hacking Social Security Numbers
Now that we have discussed some basic Google search techniques, let’s look at more advanced Google hacking. If you have never visited the Google Hacking Database (GHDB) repositories, we suggest that you visit https://www.exploit-db.com/google-hacking-database/. This site has the following search categories:
Footholds
Files containing usernames
Sensitive directories
Web server detection
Vulnerable files
Vulnerable servers
Error messages
Files containing juicy info
Files containing passwords
Sensitive online shopping info
Network or vulnerability data
Pages containing login portals
Various online devices
Advisories and vulnerabilities
A tool such as the GHDB has made using Google easier, but it’s not your only option. Maltego, FOCA, Recon Dog, and Shodan are others worth discussion. Maltego is an open source intelligence and forensics application. It is a tool-based approach to mining and gathering Internet data that can be compiled in an easy-to-understand format. Maltego offers plenty of data on websites and their services. Figure 3-4 shows an example of using Maltego to gather information about a person (in this case, Omar Santos).
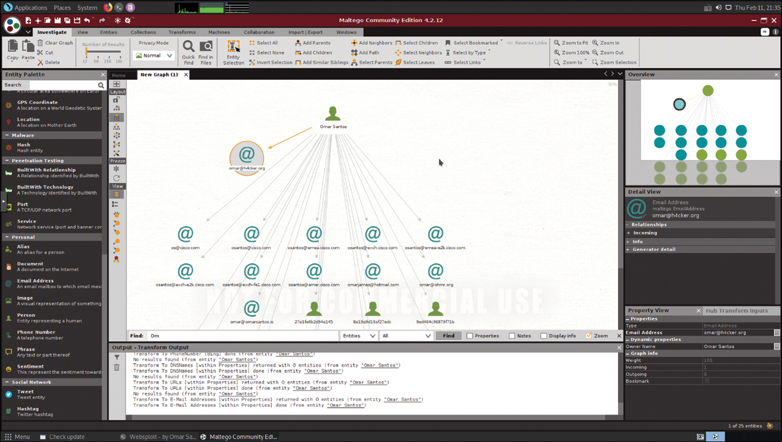
Figure 3-4 A Person Search in Maltego
FOCA is another example of an open source information-gathering tool. Similar to FOCA is Recon Dog, which is another example of an all-in-one information-gathering tool.
Shodan offers the capability to search for the servers, webcams, printers, routers, and even SCADA devices connected to the Internet. Shodan is an organization that scans the Internet on a 24/7 basis from numerous locations around the world. The scan results are then stored in a database, and you are able to search those results via the website at https://www.shodan.io or via its API.
Figure 3-5 shows an example of searching for potentially vulnerable systems in Shodan.
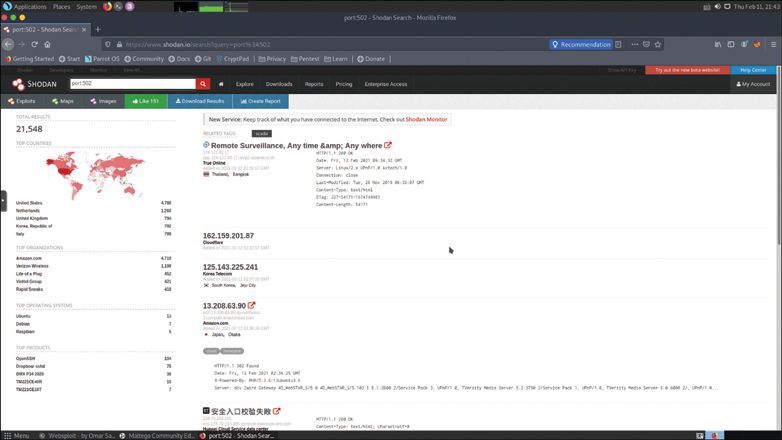
Figure 3-5 The Shodan Search Engine
In Figure 3-5, the user queries for TCP port 502, which is typically used for Modbus communication.
Tools like Shodan can be used to find network-connected devices, such as routers, servers, IoT devices, printers, databases, and even live webcams. The Shodan search engine is a powerful database of prescanned networked devices connected to the Internet. It consists of banners collected from port scans of public IP addresses, with fingerprints of services like Telnet, FTP, HTTP, and other applications.
Shodan creates risk by providing both attackers and defenders a prescanned inventory of devices connected to public IP addresses on the Internet. For example, when a new vulnerability is discovered and published, an attacker can quickly and easily search Shodan for vulnerable versions and then launch an attack. Attackers can also search the Shodan database for devices with poor configurations or other weaknesses, all without actively scanning.
Using Shodan search filters, you can really narrow down search results, by country code or CIDR netblock, for example. Shodan application programming interfaces (APIs) and some basic scripting can enable many search queries and subsequent actions (for example, a weekly query of newly discovered IPs scanned by Shodan on your CIDR netblock that runs automatically and is emailed to the security team).
Remember that public IP addresses are constantly probed and scanned already; by using Shodan, you are not scanning, because Shodan has already scanned these IPs. Shodan is a tool, and it can be used for good or evil. To mitigate risk, you can take tangible steps like registering for a free Shodan account, searching for your organization’s public IPs, and informing the right network and security people of the risks of your organization’s Shodan exposure. Using a variety of filters, these search engines allow you to query hosts and networks for specific information.
Footprinting Through Social Networking Sites
Social networks are another big target for attackers. Although social media has opened up great channels for communication and is very useful for marketers, it is fraught with potential security problems. Social networking sites are becoming one of the biggest threats to a user’s security and will remain so for the foreseeable future. One reason is that users don’t always think about security when using these sites. There is also the issue that these sites are designed to connect people. Security is not always the primary concern. Some sites that you, as an ethical hacker, might want to check include the following:
Facebook
Twitter
LinkedIn
TikTok
Pinterest
Although some organizations might be relatively secure, gaining the names, addresses, and locations of key employees can allow attackers to fly a drone over their homes, guess passwords, or even possibly backdoor the organization through an employee’s unsecure credentials.
Footprinting Through Web Services and Websites
One of the best places to begin footprinting is an organization’s website. Search for the company’s URL with Google, Bing, Dogpile, Shodan, or your search engine of choice. You will want to look for the following:
Company URL: Domain name.
Internal URLs: As an example, not only secretcorp.org but also internal.secretcorp.org, mail.secretcorp.org, finance-app.secretcorp.org, etc.
Restricted URLs: Any domains not accessible to the public.
Internal pages: Company news, employment opportunities, addresses, and phone numbers. Overall, you want to look for all open source information, which is information freely provided to clients, customers, or the general public.
Let’s look at an example of a local consulting company called secretcorp (secretcorp.org). A quick review of its site shows it has a news and updates section. Recent news states the following:
We are proud to have just updated all of our servers to Plesk 10.0.1. Anyone logging in to these new servers as admin should use the username of the domain, for example, secretcorp.org. The passwords have been transferred from the old servers, so no password reset should be required. We used the existing domain administrator password. Our continued alliance with Cisco has allowed us to complete our transition from Arista equipment. These upgrades, along with our addition of a third connection to the Internet, give us a high degree of fault tolerance.
You might consider this good marketing information to provide potential clients. The problem is that this information is available to anyone who browses the website. This information allows attackers to know that the new systems are Linux based and that the network equipment is all Extreme Networks. If attackers were planning to launch a denial-of-service (DoS) attack against the organization, they now know that they must knock out three nodes to the Internet. Even a competitor would benefit from this knowledge because the company is telling the competition everything about its infrastructure.
In some cases, information may have been removed from a company website. That is when the Wayback Machine, at https://archive.org, is useful to browse archived web pages that date back to 1996. It’s a useful tool for looking for information that no longer exists on a site.
Another big information leakage point is company directories. They usually identify key employees or departments. By combining this information with a little social engineering, an attacker can call the help desk, pretend he works for one of these key employees, and demand that a password is reset or changed. He could also use biographical information about a key employee to perform other types of social engineering trickery. During a pen test, you want to record any such findings and make sure to alert the organization as to what information is available and how it might be used in an attack.
One method to gain additional information about the organization’s email server is to send an email that will bounce from the site. If the site is secretcorp.org, send a mail to badaddress@secretcorp.org. It will bounce back to you and give you information in its header, including the email server IP address and email server version. Another great reason for bouncing an email message is to find out whether the organization makes use of mail scrubbers. Whatever you find, you should copy the information from the headers and make a note of it as you continue to gather information.
Finally, keep in mind that it’s not just logical information that you want to gather. Now is a good time to record all physical information about the targeted company. Location information is used to determine the physical location of the targeted company. Bing Maps and Google Earth are two tools that can be used to get physical layout information. Bing Maps is particularly interesting because it offers a 45-degree perspective, which gives a unique view of facilities and physical landmarks. This view enables you to identify objects such as entry points and points of ingress/egress.
If you’re lucky, the company has a job posting board. Look this over carefully; you will be surprised at how much information is given there. If no job listings are posted on the organization’s website, get interactive and check out some of the major Internet job boards. Popular sites include the following:
At the job posting site, query for the organization. Here’s an example of the type of information usually found:
Primary responsibilities for this position include management of a Windows Active Directory environment, applications running in Azure, Cisco Firepower Threat Defense (FTD) firewalls.
Interact with the technical support supervisor to resolve issues and evaluate/maintain patch level and security updates.
Experience necessary in Active Directory, Microsoft Clustering and F5 Network Load Balancing, Cisco Firepower Threat Defense (FTD) firewalls, Azure Cosmos DB, and Azure Kubernetes Service (AKS).
Maintain, support, and troubleshoot a Windows 10 user environment, Cisco SSL VPNs, firewalls, and legacy F5 load balancers.
Does this organization give away any information that might be valuable to an attacker? It actually tells attackers almost everything about its network.
One way to reduce the information leakage from job postings is to reduce the system-specific information in the job post or to use a company confidential job posting. Company confidential postings hide the true company’s identity and make it harder for attackers to misuse this type of information.
If the organization you are working for is publicly traded, you should review the Security and Exchange Commission’s EDGAR database. It’s located at https://www.sec.gov/edgar/searchedgar/companysearch.html. A ton of information is available at this site. Hackers focus on the 10-Q and 10-K. These two documents contain yearly and quarterly reports.
Not only do these documents contain earnings and potential revenue, they also contain details about any acquisitions and mergers. Anytime there is a merger, or one firm acquires another, there is a rush to integrate the two networks. Having the networks integrated is more of an immediate concern than security. Therefore, you will be looking for entity names that are different from the parent organization. These findings might help you discover ways to jump from the subsidiary to the more secure parent company. You should record this information and have it ready when you start to research the Internet Assigned Numbers Authority (IANA) and American Registry for Internet Numbers (ARIN) databases. Here are some other sites you can use to gather financial information about an organization:
Marketwatch: http://www.marketwatch.com
Experian: http://www.experian.com
Wall Street Consensus Monitor: http://www.wallstreetconsensusmonitor.com/
Euromonitor: http://www.euromonitor.com
Email Footprinting
Security is not just about technical and physical controls. It’s also about people. In many modern attacks, people are the initial target. All this really means is that an ethical hacker is also going to want to see what information is available about key personnel. Whereas websites, employee directories, and press releases may provide employee names, third-party sites have the potential to provide sensitive data an attacker might be able to leverage. We can categorize these sites as either data aggregation brokers or social networking.
A staggering number of data aggregation brokerage sites are on the web. It is easy for an attacker to perform online searches about a person. These sites allow attackers to locate key individuals, identify home phone numbers, and even create maps to people’s houses. Attackers can even see the surroundings of the company or the home they are targeting with great quality satellite pictures. Here are some of the sites:
Pipl: https://pipl.com
Spokeo: https://www.spokeo.com
Whitepages: https://www.whitepages.com
People Search Now: https://www.peoplesearchnow.com
Zabasearch: https://www.zabasearch.com
Peoplefinders: https://www.peoplefinders.com
OSINT Framework: https://osintframework.com
What’s interesting is that many sites promise everything from criminal background checks to previous addresses to marriage records to names of family members. Figure 3-6 shows an example of a Zabasearch query.
Figure 3-6 Zabasearch
Whois Footprinting
Not long ago, searching for domain name information was much easier. There were only a few places to obtain domain names, and the activities of spammers and hackers had yet to cause the Internet Assigned Numbers Authority (IANA) to restrict the release of this information. Today, the Internet Corporation for Assigned Names and Numbers (ICANN) is the primary body charged with management of IP address space allocation, protocol parameter assignment, and domain name system management. Its role is that of overall management, as domain name registration is handled by a number of competing firms that offer various value-added services. These include firms such as Network Solutions (https://www.networksolutions.com), Register.com (https://www.register.com), GoDaddy (https://www.godaddy.com), and Tucows (http://tucows.com). There is also a series of Regional Internet Registries (RIRs) that manage, distribute, and register public IP addresses within their respective regions. The five RIRs are shown in Table 3-4.
Table 3-4 RIRs and Their Area of Control
RIR |
Region of Control |
|---|---|
ARIN |
North and South America and sub-Saharan Africa |
APNIC |
Asia and Pacific |
RIPE |
Europe, Middle East, and parts of Africa |
LACNIC |
Latin America and the Caribbean |
AfriNIC |
Planned RIR to support Africa |
The primary tool to navigate these databases is Whois. Whois is a utility that interrogates the Internet domain name administration system and returns the domain ownership, address, location, phone number, and other details about a specified domain name. Whois is the primary tool used to query Domain Name System (DNS). If you’re performing this information gathering from a Linux computer, the good news is that Whois is built in. From the Linux prompt, you can type whois domainname.com or whois? to get a list of various options. Windows users are not as fortunate because Windows does not have a built-in Whois client. If you use Windows, you have to use a third-party tool or website to obtain Whois information.
One tool that a Windows user can use to perform Whois lookups is SmartWhois. You can download it from http://www.tamos.com/products/smartwhois/. SmartWhois is a useful network information utility that allows you to look up all the available information about an IP address, hostname, or domain, including country, state or province, city, name of the network provider, administrator, and technical support contact information. Several commercial and open-source tools (such as whois.domaintools.com) incorporate whois lookups. Regardless of the tool, the goal is to obtain registrar information. As a demonstration, Example 3-1 shows the results of a whois query about pearson.com.
Example 3-1 whois Query Results
> whois pearson.com % IANA WHOIS server % for more information on IANA, visit http://www.iana.org % This query returned 1 object refer: whois.verisign-grs.com domain: COM Domain Name: PEARSON.COM Registry Domain ID: 2203864_DOMAIN_COM-VRSN Registrar WHOIS Server: whois.corporatedomains.com Registrar URL: http://cscdbs.com Updated Date: 2017-02-21T19:42:01Z Creation Date: 1996-11-25T05:00:00Z Registry Expiry Date: 2022-11-24T05:00:00Z Registrar: CSC Corporate Domains, Inc. Registrar IANA ID: 299 Registrar Abuse Contact Email: domainabuse@cscglobal.com Registrar Abuse Contact Phone: 8887802723 Domain Status: clientTransferProhibited https://icann.org/epp# clientTransferProhibited Domain Status: serverDeleteProhibited https://icann.org/epp# serverDeleteProhibited Domain Status: serverTransferProhibited https://icann.org/epp# serverTransferProhibited Domain Status: serverUpdateProhibited https://icann.org/epp# serverUpdateProhibited Name Server: NS01.PEARSON.COM Name Server: NS02.PEARSON.COM Name Server: NS03.PEARSON.COM Name Server: NS04.PEARSON.COM DNSSEC: unsigned URL of the ICANN Whois Inaccuracy Complaint Form: https://www.icann.org/wicf/ >>> Last update of whois database: 2021-02-12T03:16:43Z <<< # whois.corporatedomains.com Domain Name: pearson.com Registry Domain ID: 2203864_DOMAIN_COM-VRSN Registrar WHOIS Server: whois.corporatedomains.com Registrar URL: www.cscprotectsbrands.com Updated Date: 2020-10-20T11:53:46Z Creation Date: 1996-11-25T00:00:00.000-04:00 Registrar Registration Expiration Date: 2022-11-24T00:00:00.000-04:00 Registrar: CSC CORPORATE DOMAINS, INC. Registrar IANA ID: 299 Registrar Abuse Contact Email: domainabuse@cscglobal.com Registrar Abuse Contact Phone: +1.8887802723 Domain Status: clientTransferProhibited http://www.icann.org/ epp#clientTransferProhibited Domain Status: serverDeleteProhibited http://www.icann.org/ epp#serverDeleteProhibited Domain Status: serverTransferProhibited http://www.icann.org/ epp#serverTransferProhibited Domain Status: serverUpdateProhibited http://www.icann.org/ epp#serverUpdateProhibited Registry Registrant ID: Registrant Name: Domain Management Registrant Organization: Pearson plc Registrant Street: 80 Strand Registrant City: London Registrant State/Province: ENG Registrant Postal Code: WC2R 0RL Registrant Country: GB Registrant Phone: +44.2070102000 Registrant Phone Ext: Registrant Fax: +44.2070106060 Registrant Fax Ext: Registrant Email: domain.management@pearson.com Registry Admin ID: Admin Name: Domain Management Admin Organization: Pearson plc Admin Street: 80 Strand Admin City: London Admin State/Province: ENG Admin Postal Code: WC2R 0RL Admin Country: GB Admin Phone: +44.2070102000 Admin Phone Ext: Admin Fax: +44.2070106060 Admin Fax Ext: Admin Email: domain.management@pearson.com Registry Tech ID: Tech Name: Domain Management Tech Organization: Pearson plc Tech Street: 80 Strand Tech City: London Tech State/Province: ENG Tech Postal Code: WC2R 0RL Tech Country: GB Tech Phone: +44.2070102000 Tech Phone Ext: Tech Fax: +44.2070106060 Tech Fax Ext: Tech Email: domain.management@pearson.com Name Server: ns01.pearson.com Name Server: ns02.pearson.com Name Server: ns03.pearson.com Name Server: ns04.pearson.com DNSSEC: unsigned
This information provides a contact, address, phone number, and DNS servers. A hacker skilled in the art of social engineering might use this information to call the organization and pretend to be a valid contact.
DNS Footprinting
If all the previous information has been acquired, the DNS might be targeted for zone transfers. A zone transfer is the mechanism used by DNS servers to update each other by transferring the contents of their database. DNS is structured as a hierarchy so that when you request DNS information, your request is passed up the hierarchy until a DNS server is found that can resolve the domain name request. You can get a better idea of how DNS is structured by examining Figure 3-7, which shows the DNS server hierarchy (structure).
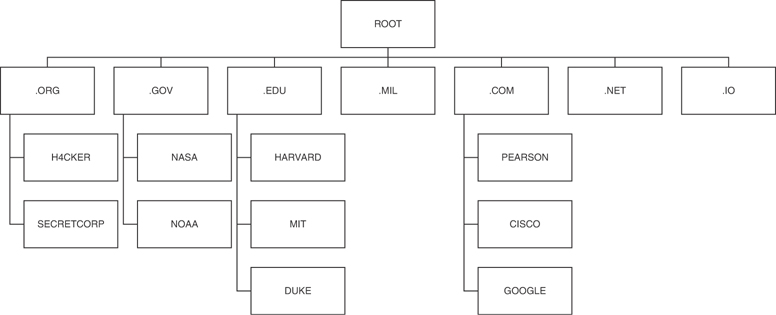
Figure 3-7 DNS Structure
What’s left at this step is to try to gather additional information from the organization’s DNS servers. The primary tool to query DNS servers is Nslookup. Nslookup provides machine name and address information. Both Linux and Windows have Nslookup clients. You use Nslookup by typing nslookup at the command line followed by an IP address or a machine name. Doing so causes Nslookup to return the name, all known IP addresses, and all known CNAMEs for the identified machine. Nslookup queries DNS servers for machine name and address information. Using Nslookup is rather straightforward. Let’s look at an example in which Nslookup is used to find the IP addresses of Google’s web servers. If you enter nslookup google.com, you will see the response in Example 3-2.
Example 3-2 Nslookup google.com Reply
$ nslookup google.com Server: 208.67.222.222 Address: 208.67.222.222#53 Non-authoritative answer: Name: google.com Address: 172.217.8.14
The first two lines of output say which DNS servers are being queried. In this case, it’s OpenDNS. The nonauthoritative answer lists two IP addresses for the Google’s web servers. Responses from nonauthoritative servers do not contain copies of any domains. They have a cache file that is constructed from all the DNS lookups it has performed in the past for which it has gotten an authoritative response.
Nslookup can also be used in an interactive mode; you just type nslookup at the command prompt in Windows or the Linux or macOS shell. In interactive mode, you will be given a prompt of >; at which point, you can enter a variety of options, including attempts to perform a zone transfer. Table 3-5 shows some common DNS resource record names and types.
Table 3-5 IPv4 DNS Records and Types
Record Name |
Record Type |
Purpose |
|---|---|---|
Host |
A |
Maps a domain name to an IPv4 address |
Host |
AAAA |
Maps a domain name to an IPv6 address |
Pointer |
PTR |
Maps an IP address to a domain name |
Name Server |
NS |
Specifies the servers that provide DNS services |
Start of Authority |
SOA |
Configures settings for zone transfers and record caching |
Service Locator |
SRV |
Used to locate services in the network |
MX |
Used to identify SMTP servers |
DNS normally moves information from one DNS server to another through the DNS zone transfer process. If a domain contains more than one name server, only one of these servers will be the primary. Any other servers in the domain will be secondary servers. Zone transfers are much like the DHCP process in that each is a four-step process. DNS zone transfers function as follows:
The secondary name server starts the process by requesting the SOA record from the primary name server.
The primary then checks the list of authorized servers, and if the secondary server’s name is on that list, the SOA record is sent.
The secondary must then check the SOA record to see whether there is a match against the SOA it already maintains. If the SOA is a match, the process stops here; however, if the SOA has a serial number that is higher, the secondary will need an update. The serial number indicates if changes were made since the last time the secondary server synchronized with the primary server. If an update is required, the secondary name server will send an All Zone Transfer (AXFR) request to the primary server.
Upon receipt of the AXFR, the primary server sends the entire zone file to the secondary name server.
A zone transfer is unlike a normal lookup in that the user is attempting to retrieve a copy of the entire zone file for a domain from a DNS server. This can provide a hacker or pen tester with a wealth of information. This is not something that the target organization should be allowing. Unlike lookups that primarily occur on UDP 53, unless the response is greater than 512 bytes, zone transfers use TCP 53. To attempt a zone transfer, you must be connected to a DNS server that is the authoritative server for that zone. Example 3-3 demonstrates a DNS Zone transfer using the ZoneTransfer.me domain:
Example 3-3 Zone Transfer
$ dig axfr @nsztm1.digi.ninja zonetransfer.me
; <<>> DiG 9.16.6-Debian <<>> axfr @nsztm1.digi.ninja zonetransfer.me
; (1 server found)
;; global options: +cmd
zonetransfer.me. 7200 IN SOA nsztm1.digi.ninja. robin.digi.
ninja. 2019100801 172800 900 1209600 3600
zonetransfer.me. 300 IN HINFO "Casio fx-700G" "Windows
XP"
zonetransfer.me. 301 IN TXT "google-site-verification=tyP
28J7JAUHA9fw2sHXMgcCC0I6XBmmoVi04VlMewxA"
zonetransfer.me. 7200 IN MX 0 ASPMX.L.GOOGLE.COM.
zonetransfer.me. 7200 IN MX 10 ALT1.ASPMX.L.GOOGLE.COM.
zonetransfer.me. 7200 IN MX 10 ALT2.ASPMX.L.GOOGLE.COM.
zonetransfer.me. 7200 IN MX 20 ASPMX2.GOOGLEMAIL.COM.
zonetransfer.me. 7200 IN MX 20 ASPMX3.GOOGLEMAIL.COM.
zonetransfer.me. 7200 IN MX 20 ASPMX4.GOOGLEMAIL.COM.
zonetransfer.me. 7200 IN MX 20 ASPMX5.GOOGLEMAIL.COM.
zonetransfer.me. 7200 IN A 5.196.105.14
zonetransfer.me. 7200 IN NS nsztm1.digi.ninja.
zonetransfer.me. 7200 IN NS nsztm2.digi.ninja.
_acme-challenge.zonetransfer.me. 301 IN TXT
"6Oa05hbUJ9xSsvYy7pApQvwCUSSGgxvrbdizjePEsZI"
_sip._tcp.zonetransfer.me. 14000 IN SRV 0 0 5060 www.
zonetransfer.me.
14.105.196.5.IN-ADDR.ARPA.zonetransfer.me. 7200 IN PTR www.
zonetransfer.me.
asfdbauthdns.zonetransfer.me. 7900 IN AFSDB 1 asfdbbox.
zonetransfer.me.
asfdbbox.zonetransfer.me. 7200 IN A 127.0.0.1
asfdbvolume.zonetransfer.me. 7800 IN AFSDB 1 asfdbbox.
zonetransfer.me.
canberra-office.zonetransfer.me. 7200 IN A 202.14.81.230
cmdexec.zonetransfer.me. 300 IN TXT "; ls"
contact.zonetransfer.me. 2592000 IN TXT "Remember to call or
email Pippa on +44 123 4567890 or pippa@zonetransfer.me when making
DNS changes"
dc-office.zonetransfer.me. 7200 IN A 143.228.181.132
deadbeef.zonetransfer.me. 7201 IN AAAA dead:beaf::
dr.zonetransfer.me. 300 IN LOC 53 20 56.558 N 1 38
33.526 W 0.00m 1m 10000m 10m
DZC.zonetransfer.me. 7200 IN TXT "AbCdEfG"
email.zonetransfer.me. 2222 IN NAPTR 1 1 "P" "E2U+email"
"" email.zonetransfer.me.zonetransfer.me.
email.zonetransfer.me. 7200 IN A 74.125.206.26
Hello.zonetransfer.me. 7200 IN TXT "Hi to Josh and all
his class"
home.zonetransfer.me. 7200 IN A 127.0.0.1
Info.zonetransfer.me. 7200 IN TXT "ZoneTransfer.me
service provided by Robin Wood - robin@digi.ninja. See http://digi.
ninja/projects/zonetransferme.php for more information."
internal.zonetransfer.me. 300 IN NS intns1.zonetransfer.me.
internal.zonetransfer.me. 300 IN NS intns2.zonetransfer.me.
intns1.zonetransfer.me. 300 IN A 81.4.108.41
intns2.zonetransfer.me. 300 IN A 167.88.42.94
office.zonetransfer.me. 7200 IN A 4.23.39.254
ipv6actnow.org.zonetransfer.me. 7200 IN AAAA
2001:67c:2e8:11::c100:1332
owa.zonetransfer.me. 7200 IN A 207.46.197.32
robinwood.zonetransfer.me. 302 IN TXT "Robin Wood"
rp.zonetransfer.me. 321 IN RP robin.zonetransfer.me.
robinwood.zonetransfer.me.
sip.zonetransfer.me. 3333 IN NAPTR 2 3 "P" "E2U+sip"
"!^.*$!sip:customer-service@zonetransfer.me!" .
sqli.zonetransfer.me. 300 IN TXT "' or 1=1 --"
sshock.zonetransfer.me. 7200 IN TXT "() { :]}; echo
ShellShocked"
staging.zonetransfer.me. 7200 IN CNAME www.
sydneyoperahouse.com.
alltcpportsopen.firewall.test.zonetransfer.me. 301 IN A 127.0.0.1
testing.zonetransfer.me. 301 IN CNAME www.zonetransfer.
me.
vpn.zonetransfer.me. 4000 IN A 174.36.59.154
www.zonetransfer.me. 7200 IN A 5.196.105.14
xss.zonetransfer.me. 300 IN TXT "'><script>alert('Boo')</
script>"
zonetransfer.me. 7200 IN SOA nsztm1.digi.ninja.
robin.digi.ninja. 2019100801 172800 900 1209600 3600
;; Query time: 92 msec
;; SERVER: 81.4.108.41#53(81.4.108.41)
;; XFR size: 50 records (messages 1, bytes 1994
One of two things will happen at this point. You will receive an error message indicating that the transfer was unsuccessful, or you will be returned a wealth of information, as shown in the query in Example 3-4 for the domain h4cker.org.
Example 3-4 Using Nslookup to Resolve DNS Names
$ nslookup h4cker.org Server: 208.67.222.222 Address: 208.67.222.222#53 Non-authoritative answer: Name: h4cker.org Address: 185.199.109.153 Name: h4cker.org Address: 185.199.110.153 Name: h4cker.org Address: 185.199.111.153 Name: h4cker.org Address: 185.199.108.153
Dig is another tool that you can use to provide this type of information. It’s built in to most Linux distributions and can be run from Bash or run from the command prompt when installed in Windows. Dig is a powerful tool that can be used to investigate the DNS system. Example 3-5 demonstrates using dig to obtain information about the domain h4cker.org.
Example 3-5 Using dig to Investigate a DNA System
$ dig h4cker.org ; <<>> DiG 9.10.6 <<>> h4cker.org ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 42293 ;; flags: qr rd ra ad; QUERY: 1, ANSWER: 4, AUTHORITY: 0, ADDITIONAL: 1 ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 4096 ;; QUESTION SECTION: ;h4cker.org. IN A ;; ANSWER SECTION: h4cker.org. 300 IN A 185.199.110.153 h4cker.org. 300 IN A 185.199.111.153 h4cker.org. 300 IN A 185.199.108.153 h4cker.org. 300 IN A 185.199.109.153 ;; Query time: 73 msec ;; SERVER: 208.67.222.222#53(208.67.222.222) ;; WHEN: Thu Feb 11 22:24:36 EST 2021 ;; MSG SIZE rcvd: 103
There is also a range of tools that can be used to interrogate DNS servers, including the following:
DomainDossier: https://centralops.net/co/domaindossier.aspx
ViewDNS: https://viewdns.info
Domain to IP Converter: https://domaintoipconverter.com
Internal DNS information should not be made available to just anyone. Hackers can use this information to find out what other servers are running on the network, and it can help them map the network and formulate what types of attacks to launch. Zone transfers are intended for use by secondary DNS servers to synchronize with their primary DNS server. You should make sure that only specific IP addresses are allowed to request zone transfers. Most operating systems restrict this by default. All DNS servers should be tested. It is often the case that the primary has tight security but the secondaries may allow zone transfers if misconfigured.
Network Footprinting
Now that the pen test team has been able to locate names, phone numbers, addresses, some server names, and IP addresses, it’s important to find out what IP addresses are available for scanning and further enumeration. If you take the IP address of a web server discovered earlier and enter it into the Whois lookup at https://www.arin.net, you can determine the network’s range. In the example in Figure 3-8, the IP address 157.245.123.123 was entered into the ARIN Whois, so now you can see the details about who owns that IP block. In this case, the IP block 157.245.0.0/16 was allocated to Digital Ocean (a cloud service provider).
An attacker can now focus his efforts on the range from 157.245.0.1 to 157.245.255.254. If these results don’t prove satisfactory, the attacker can use traceroute for additional mapping.
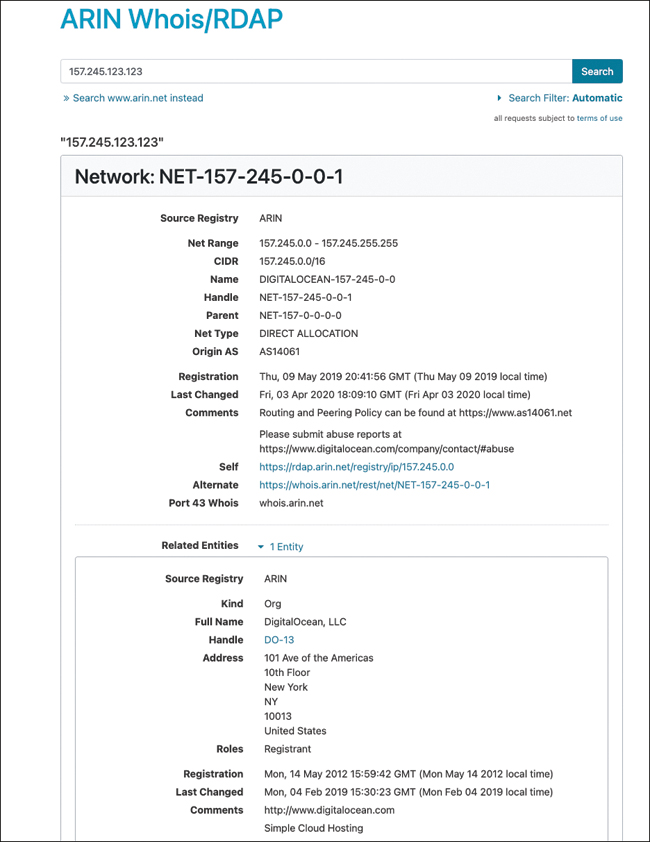
Figure 3-8 ARIN’s Whois Lookup
Subnetting’s Role in Mapping Networks
Some of the items you might see on the exam but are not included in any of the official courseware include subnetting. Subnetting allows the creation of many logical networks that exist within a single Class A, B, or C network. Subnetting is important in that it helps pen testers identify what systems are part of which specific network.
To subnet a network, you must extend the natural mask with some of the bits from the host ID portion of the address. For example, if you had a Class C network of 192.168.5.0, which has a natural mask of 255.255.255.0, you can create subnets in this manner:
192.168.5.0 -11001100.10101000.00000101.00000000 255.255.255.224 - 11111111.11111111.11111111.11100000 ------------------------------------------------|subnet|----
By extending the mask from 255.255.255.0 to 255.255.255.224, you have taken 3 bits from the original host portion of the address and used them to make subnets. When you borrow these 3 bits, it is possible to create eight subnets. The remaining 5 bits can provide up to 32 host addresses, 30 of which can actually be assigned to a device because host addresses with all zeros and all ones are not assigned to specific devices. Here is a breakdown of the subnets and their address ranges:
Subnet |
Host Range |
|---|---|
192.168.5.0 255.255.255.224 |
Host address range 1 to 30 |
192.168.5.32 255.255.255.224 |
Host address range 33 to 62 |
192.168.5.64 255.255.255.224 |
Host address range 65 to 94 |
192.168.5.96 255.255.255.224 |
Host address range 97 to 126 |
192.168.5.128 255.255.255.224 |
Host address range 129 to 158 |
192.168.5.160 255.255.255.224 |
Host address range 161 to 190 |
192.168.5.192 255.255.255.224 |
Host address range 193 to 222 |
192.168.5.224 255.255.255.224 |
Host address range 225 to 254 |
The more host bits you use for a subnet mask, the more subnets you have available. However, the more subnets that are available, the fewer host addresses that are available per subnet.
Traceroute
It’s advisable to check out more than one version of traceroute if you don’t get the required results. Some techniques can also be used to try to slip traceroute past a firewall or filtering device. When UDP and ICMP are not allowed on the remote gateway, you can use the Linux tcptraceroute command, which allows you to use TCP packets for traceroute. You can obtain more information about tcptraceroute at https://linux.die.net/man/1/tcptraceroute. Another unique technique was developed by Michael Schiffman, who created a patch called traceroute.diff that allows you to specify the port that traceroute will use. With this handy tool, you could easily direct traceroute to use UDP port 53. Because that port is used for DNS queries, there’s a good chance that it could be used to slip past the firewall. If you’re looking for a graphical user interface (GUI) program to perform traceroute with, several are available, as described here:
LoriotPro: A professional and scalable SNMP manager and network monitoring solution that enables availability and performance control of your networks, systems, and smart infrastructures. The graphical display shows you the route between you and the remote site, including all intermediate nodes and their registrant information.
Trout: A visual traceroute and Whois program. What’s great about this program is its speed. Unlike traditional traceroute programs, Trout performs parallel pinging. By sending packets with more than one TTL at a time, it can quickly determine the path to a targeted device.
VisualRoute: Another graphical traceroute for Windows. VisualRoute not only shows a graphical world map that displays the path that packets are taking but also lists information for each hop, including IP address, node name, and geographic location. This tool is commercial and must be purchased.
Footprinting Through Social Engineering
An attacker can also reveal a lot of information about the targeted organization and underlying systems by using social engineering. The reason is that, in many cases, it is even easier to get sensitive information by tricking a human in a conversation or by sending an email instead of using sophisticated scanning and enumeration tools.
You will learn the details about social engineering tactics and techniques in Chapter 5, “Social Engineering, Malware Threats, and Vulnerability Analysis.”
Footprinting Countermeasures
The following are some of the most common countermeasures to protect your organizations and employees from malicious footprinting:
Provide user education to stay safe online. In the past, many companies restricted employees from accessing social networking sites from their network. However, nowadays social networking sites are used as marketing tools and have become essential for business. This is why user education in some cases is better than completely blocking social networking sites.
Configure web servers to avoid information leakage.
Educate employees to use pseudonyms on blogs, groups, and forums.
Do not reveal critical information in press releases, annual reports, product catalogs, and so on.
As an ethical hacker, use footprinting techniques to discover and remove any sensitive information about your company and systems that is publicly available.
Prevent search engines from caching your websites and use anonymous registration services.
Enforce security policies to regulate the information that your users can reveal to third parties.
Configure separate internal and external DNS, or use split DNS and restrict zone transfer to authorized servers.
Disable directory listings in the web servers.
Educate users about social engineering risks.
Subscribe to use domain registration privacy services on the Whois Lookup database.
Prevent domain-level cross-linking for the critical assets.
