Review Questions
Your client has asked you to run an Nmap scan against the servers it has located in its DMZ. The client would like you to identify the OS. Which of the following switches would be your best option?
nmap -P0
nmap -sO
nmap -sS
nmap -O
During an internal pen test, you have gained access to an internal switch. You have been able to SPAN a port and are now monitoring all traffic with Wireshark. While reviewing this traffic, you are able to identify the OS of the devices that are communicating. What best describes this activity?
Vulnerability scanning
Nmap port scanning
Active OS fingerprinting
Passive OS fingerprinting
ICMP is a valuable tool for troubleshooting and reconnaissance. What is the correct type for a ping request and a ping response?
Ping request type 5, ping reply type 3
Ping request type 8, ping reply type 0
Ping request type 3, ping reply type 5
Ping request type 0, ping reply type 8
Which of the following is a vulnerability in the Bash shell that was discovered in 2014 and thereafter exploited to launch a range of attacks against Linux and UNIX systems?
Shellshock
Heartbleed
Bashshell
Poodle
As part of a pen test, you have port scanned a Linux system. Listed here is the scan you performed: nmap -sX -vv -P0 192.168.1.123 -p 80. If the system had the specific listening port open, what would be returned?
RST
No response
SYN ACK
ACK
Which of the following Netcat commands could be used to perform a UDP scan of the lower 1024 ports?
Nc -sS -O target 1-1024
Nc -hU <host(s)>
Nc -sU -p 1-1024 <host(s)>
Nc -u -v -w2 <host> 1-1024
You have been assigned a junior pen tester during a pen test. You performed the following scan:
nmap -sL www.example.com Starting Nmap 6.25 ( http://nmap.org ) at 2016-10-12 18:46 Central Daylight Time Host 93.184.216.34 not scanned
Your partner asks you to explain the results. Which of the following best describes the correct answer?
The system was offline.
The technique only checks DNS and does not scan.
The syntax is incorrect.
ICMP is blocked, so no scan is performed.
Which of the following sets all TCP flags to zeros?
nmap -sn 192.168.1.1/24
nmap -null 192.168.1.1/24
nmap -sX 192.168.1.1/24
nmap -sI 192.168.1.1/24
You have captured some packets from a system you would like to passively fingerprint. You noticed that the IP header length is 20 bytes and there is a datagram length of 84 bytes. What do you believe the system to be?
Windows XP
Linux
Windows 7
Windows 8
During the network mapping phase of a pen test, you have discovered the following two IP addresses: 192.168.1.24 and 192.168.1.35. They both have a mask of 255.255.255.224. Which of the following is true?
They are on the same network.
They both have a default gateway of 192.168.1.63.
They both have a default gateway of 192.168.1.254.
They are on separate subnets.
What type of scan is harder to perform because of the lack of response from open services and because packets could be lost due to congestion or from firewall blocked ports?
Stealth scanning
ACK scanning
UDP scanning
FIN scan
You would like to perform a scan that runs a script against SSH and attempts to extract the SSH host key. Which of the following is the correct syntax?
nmap -sC -p21, 111, 139 -T3 www.knowthetrade.com
nmap -sC -p22, 111, 139 -T4 www.knowthetrade.com
nmap -sL -p21, 111, 139 -T3 www.knowthetrade.com
nmap -sI -p22, 111, 139 -T4 www.knowthetrade.com
You have just performed an ACK scan and have been monitoring a sniffer while the scan was performed. The sniffer captured the result of the scan as an ICMP type 3 code 13. What does this result mean?
The firewall is only a router with an ACL.
The port is open.
Port knocking is used.
The port is closed.
One of the members of your security assessment team is trying to find out more information about a client’s website. The Brazilian-based site has a .com extension. She has decided to use some online Whois tools and look in one of the Regional Internet Registries. Which of the following represents the logical starting point?
AfriNIC
ARIN
APNIC
RIPE
You have captured the Wireshark scan results shown in Figure 3-13 and are attempting to determine what type of scan was performed against the targeted system. What is your answer?
SYN
IPID
NULL
XMAS
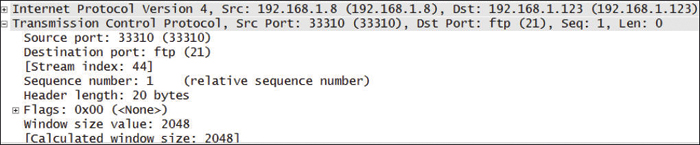
Figure 3-13 Wireshark Scan Capture
What is the purpose of the following Nmap scan?
Nmap -sn 192.168.123.1-254
Ping only on the targets, no port scan
A NULL TCP scan
A TCP port scan
Port scan all targets
You’re starting a port scan of a new network. Which of the following can be used to scan all ports on the 192.168.123.1 network?
nmap -p 1,65536 192.168.123.1
nmap -p- 192.168.123.1
nmap 192.168.123.1 -ports "all"
nmap -p 0-65536 192.168.123.1
Which of following port-scanning techniques can be used to map out the firewall rules on a router?
NULL scan
ACK scan
Inverse flag scan
Firewalk
What are the two ICMP codes used when performing a ping?
Type 0 and 8
Type 0 and 3
Type 3 and 5
Type 5 and 11
You have successfully scanned a system and identified the following port 80 open. What is the next step you should perform?
Attempt to go to the web page and examine the source code.
Use FTP to connect to port 80.
Telnet to the open port and grab the banner.
Attempt to connect to port 443.
