- "Do I Know This Already?" Quiz
- Physical Security Measures
- Logical Security Concepts
- Wireless Security Protocols and Authentication
- Malware Removal and Prevention
- Social Engineering Threats and Vulnerabilities
- Microsoft Windows OS Security Settings
- Security Best Practices to Secure a Workstation
- Securing Mobile Devices
- Data Destruction and Disposal
- Configuring Security on SOHO Networks
- Exam Preparation Tasks
- Review All the Key Topics
- Define Key Terms
- Answer Review Questions
Configuring Security on SOHO Networks
220-1002: Objective 2.10: Given a scenario, configure security on SOHO wireless and wired networks.
Both wireless and wired small office/home office (SOHO) networks are important to businesses of all sizes as well as individual users. However, they also represent significant vulnerabilities if they are not properly secured. The following sections explain how the different encryption methods work and the additional steps that must be taken to completely secure a wireless network.
Wireless-Specific Security
The default settings for a wireless network should be changed to provide security. The following sections discuss these issues.
Changing Default SSID
The service set identifier (SSID) can provide a great deal of useful information to a potential hacker of a wireless network. Every wireless network must have an SSID, and by default, WAPs and wireless routers typically use the manufacturer’s name or the device’s model number as the default SSID. If a default SSID is broadcast by a wireless network, a hacker can look up the documentation for a specific router or the most common models of a particular brand and determine the default IP address range, the default administrator username and password, and other information that would make it easy to attack the network.
To help “hide” the details of your network and location, a replacement SSID for a secure wireless network should not include any of the following:
Your name
Your company name
Your location
Any other easily identifiable information
An SSID that includes obscure information (such as the name of your first pet) would be a suitable replacement.
Setting Encryption
The importance of setting encryption to the latest possible standards is covered earlier in this chapter, in the section “Wireless Security Protocols and Authentication.” The information there applies to SOHO networks as well, as a SOHO may be set up as an extension of a business. In such a case, all security policies from the business should apply at the SOHO extension as well.
Disabling SSID Broadcast
Disabling SSID broadcast is widely believed to be an effective way to prevent a wireless network from being detected and is so regarded by the A+ certification exams. But that is not always enough. Even though disabling SSID broadcast prevents casual bandwidth snoopers from finding your wireless network, Microsoft does not recommend disabling SSID broadcasting as a security measure because there are methods serious hackers can use to discover networks.
Figure 7-22 illustrates a Linksys router configuration dialog in which several of these security recommendations have been implemented.
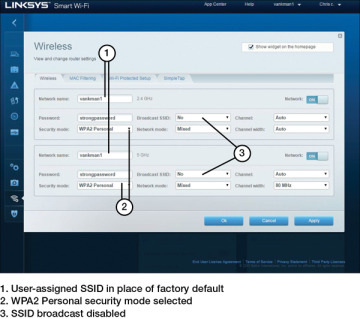
FIGURE 7-22 Configuring a Router with Alternative SSIDs, WPA2 Encryption Enabled, and SSID Broadcast Disabled
Antenna and Access Point Placement
When configuring and/or troubleshooting wireless connections, think about the wireless access point’s (WAP’s) location. The placement of the access point plays a big part in a strong signal. Generally, it should be placed in the middle of an office to offer the greatest coverage while reducing the chance of outsiders being able to connect to the device. The antennas on the access point should be set at a 90-degree angle to each other. Keep the device away from any forms of electrical interference, such as other wireless devices, speakers, and any devices that use a lot of electricity.
Radio Power Levels
Some wireless routers and access points have adjustable radio power levels. When they are set too low, clients at the perimeter of the building will not be able to gain access. When they are set too high, computers located in neighboring businesses will be able to attempt access. If a wireless signal is too weak, regardless of the router location and radio power levels, and the router is older, consider replacing it with a new wireless router.
WiFi Protected Setup (WPS)
Using WiFi Protected Setup (WPS) is an easy way to configure a secure wireless network with a SOHO router, provided that all devices on the network support WPS. There are several ways that WPS can be configured. The most common ways include:
PIN: A personal identification number (PIN) marked on the router may be entered into each new device added to the network. This is the default method.
Push button: The router or WAP may have a push button, and each new device may also have a physical push button or (more often) a software push button in the setup program. Both the button on the WAP or router and the button on the other device must be pushed within a short period of time to make the connection.
A security flaw with the PIN method was discovered, and many professionals recommend against WPS on this basis. But it really depends on the features available on the router. Some routers let you disable the PIN and allow the push-button method, but many do not. Some routers allow you to disable WPS altogether. These settings are worth investigating when looking to install or replace a WAP. Figure 7-23 depicts WiFi Protected Setup options.

FIGURE 7-23 WiFi Protected Setup Options
Change Default Usernames and Passwords
As mentioned previously, the documentation for almost all WAPs and wireless routers lists the default administrator password, and the documentation can be readily downloaded in PDF or HTML form from vendor websites. Because an attacker could use this information to “take over” the device, it is essential to change the default to a private password. Most routers use the Administration or Management dialog for the password and other security settings.
Enable MAC Filtering
As mentioned earlier in this chapter, every device on a network has a MAC address. All devices on a SOHO network, including phones and tablets, have MAC addresses as well, and they need to be managed with filtering. Refer to the section “Physical Security Measures,” earlier in this chapter, for details about software used to hack networks. MAC filtering is described in more detail in Chapter 2.
Assign Static IP Addresses
The DHCP server built into a router hands out IP addresses to all computers connected to it. This is convenient, but if you want to limit access to the Internet for certain computers or log activity for computers by IP address, the DHCP setting should be disabled, and a static IP address should be assigned to each computer. This way, outside devices will not be assigned IP addresses and be able to access the network.
Firewall Settings
By default, most WAPs and wireless routers use a feature called Network Address Translation (NAT) to act as simple firewalls. NAT prevents traffic from the Internet from determining the private IP addresses used by computers on the network. However, many WAPs and wireless routers offer additional firewall features that can be enabled, including:
Access logs
Filtering of specific types of traffic
Enhanced support for VPNs
See the router manufacturer’s documentation for more information about advanced security features. Figure 7-24 shows an example of firewall settings.

FIGURE 7-24 Firewall Settings
Port Forwarding/Mapping
Use port forwarding (also known as port mapping) to allow inbound traffic on a particular TCP or UDP port or range to go to a particular IP address rather than to all devices on a network. A basic example would be an FTP server internal to a LAN. The FTP server might have the IP address 192.168.0.250 and have port 21 open and ready to accept file transactions (or a different inbound port could be used). Clients on the Internet that want to connect to the FTP server would have to know the IP address of the router, so the clients might connect with an FTP client using the IP address 68.54.127.95 and port 21. If there is an appropriate port-forwarding rule, the router sees these packets and forwards them to 192.168.0.250:21, or whatever port is chosen. Many ISPs block this type of activity, but port forwarding is a common and important method in larger networks.
Disabling Ports
Blocking TCP and UDP ports, also known as disabling ports, is performed with a firewall app such as Windows Defender Firewall with Advanced Security. Hackers take advantage of unused ports sitting idle on a network, and disabling unnecessary ports makes it harder to access your domain.
Content Filtering/Parental Controls
Windows Defender is Microsoft’s anti-spyware tool that has evolved over the Windows releases. Windows 8 combined Windows Defender with other tools so that Windows was equipped to fight off virus attacks without any additional software. In Windows 10, the same Windows Defender protection is in place, and it has been combined with other tools and put into the Settings menu as an app. Figure 7-25 depicts the Windows Defender Security Center options. Windows Defender includes the following sections:
Virus & Threat Protection: Allows tracking of Windows Defender and third-party antivirus software
Account Protection: Includes Windows Hello and Dynamic Lock features
Firewall & Network Protection: Contains access control rules and other network and domain security settings
App & Browser Control: Contains filter controls for browsers and apps
Device Security: Tests device security and sets core security
Device Performance & Health: Scans devices and apps to report on status
Family Options: Provides parental controls and family device management options

FIGURE 7-25 Windows Defender Settings in Windows 10
Spending time getting to know the settings in the Windows Defender Security Center is a must for any technical support professional.
Apple has parental controls in macOS versions. They can be found by selecting the Apple menu > System Preferences > Parental Controls.
Linux distros do not include parental controls, but many third-party apps are available.
Update Firmware
Most SOHO router vendors issue at least one firmware update during the life span of each model of WAP and wireless router. Updates can solve operational problems and might add features that enhance WiFi interoperability, security, and ease of use. To determine whether a WAP or wireless router has a firmware update available, follow these steps:
Step 1. View the device’s configuration dialogs to record the current firmware version. Also note the router’s model number and revision from the back or bottom of the device.
Step 2. Visit the device vendor’s website to see whether a newer version of the firmware is available.
Step 3. Download the firmware update to a PC that can be connected to the device with an Ethernet cable.
Step 4. Connect the PC to the device with an Ethernet cable.
Step 5. Navigate to the device’s firmware update dialog.
Step 6. Follow the instructions to update firmware.
Physical Security
In a SOHO network environment, physical security refers to preventing unauthorized use of the network. The same basics of physical security apply in a SOHO network in a large office environment:
Secure the network equipment in a locked wiring closet or room.
Disable any unused wall Ethernet jacks by either disabling their switch ports or unplugging the patch panels in the wiring closet.
Route network cables out of sight, in the walls and above the ceiling. Having them out of sight cuts down on the chances of someone tapping into the network.
Lock doors when leaving.
If possible, dedicate a lockable room as a workspace in a home office to protect company devices and other resources from the hazards of daily family life, such as children and pets.