- Understanding the Secure Facility Layered Defense Model
- Protecting Equipment
- Summary
- Test Your Skills
- References
Protecting Equipment
Now that we have defined how facilities and work areas will be secured, we must address the security of the equipment within these facilities. Traditionally, protection controls were limited to company-owned equipment. This is no longer the case. Increasingly, organizations are encouraging employees and contractors to “bring your own device” to work (referred to as BYOD). These devices may store, process, or transmit company information. In developing policies, we need to consider how best to protect both company- and employee-owned equipment from unauthorized access, theft, damage, and destruction.
No Power, No Processing?
No power, no processing—it’s that simple. Long before computers took over the business world, organizations have been taking steps to ensure that power is available. Of course, it is now more important than ever. All information systems rely on clean, consistent, and abundant supplies of electrical power. Even portable devices that run on battery power require electricity for replenishment. Power is not free. Quite the contrary: Power can be very expensive, and excessive use has an environmental and geopolitical impact.
Power Protection
To function properly, our systems need consistent power delivered at the correct voltage level. Systems need to be protected from power loss, power degradation, and even from too much power, all of which can damage equipment. Common causes of voltage variation include lightning; damage to overhead lines from storms, trees, birds, or animals; vehicles striking poles or equipment; and load changes or equipment failure on the network. Heat waves can also contribute to power interruptions because the demand in electricity (that is, air conditioners) can sometimes exceed supply. The variation may be minor or significant.
Power fluctuations are categorized by changes in voltage and power loss. Figure 7-1 shows the difference between a power surge and a power spike.
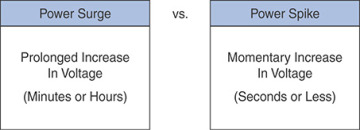
FIGURE 7-1 Power Surge vs. Power Spike
Figure 7-2 shows the difference between a brownouts and a sag.
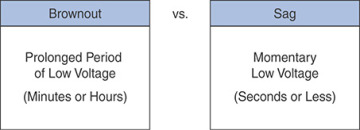
FIGURE 7-2 Brownout vs. Sag
Figure 7-3 shows the difference between a blackout and a fault.
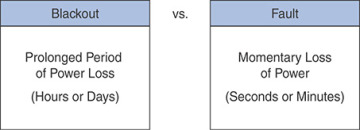
FIGURE 7-3 Blackout vs. Fault
Companies can install protective devices to help guard their premises and assets, such as installing surge protection equipment, line filters, isolation transformers, voltage regulators, power conditioners, uninterruptible power supplies (UPSs), and back-up power supplies or generators. These power protection devices can condition the feed for consistency, provide continuous power for critical systems, and manage a controlled shutdown in the event of total loss of power.
How Dangerous Is Fire?
Imagine the impact of a data center fire—equipment and data irrevocably destroyed, internal communications damaged, and external connectivity severed. On November 2017, Data Center Dynamics reported that a faulty battery in a UPS caused a fire in a health center in Cairns, Australia, causing two hospitals and several of the city’s health service systems to fail.
Fire protection is composed of the three elements shown in Figure 7-4.
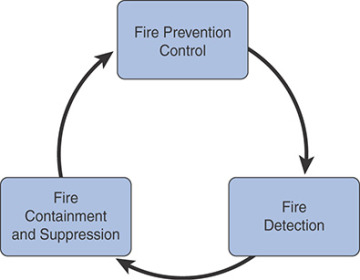
FIGURE 7-4 Fire Protection Elements
Active and passive fire prevention controls are the first line of defense. Fire prevention controls include hazard assessments and inspections, adhering to building and construction codes, using flame-retardant materials, and proper handling and storage procedures for flammable/combustible materials. Fire detection is recognizing that there is a fire. Fire detection devices can be smoke activated, heat activated, or flame activated. Fire containment and suppression involve actually responding to the fire. Containment and suppression equipment is specific to fire classification. Data center environments are typically at risk of Class A, B, or C fires:
Class A: Fire with combustible materials as its fuel source, such as wood, cloth, paper, rubber, and many plastics
Class B: Fire in flammable liquids, oils, greases, tars, oil-based paints, lacquers, and flammable gases
Class C: Fire that involves electrical equipment
Class D: Combustibles that involve metals
Facilities must comply with standards to test fire-extinguishing methods annually to validate full functionality.
The best-case scenario is that data centers and other critical locations are protected by an automatic fire-fighting system that spans multiple classes. Like all other major investments, it’s prudent to do a cost/benefit analysis before making a decision. In any emergency situation, human life always takes precedence. All personnel should know how to quickly and safely evacuate an area.
What About Disposal?
What do servers, workstations, laptops, tablets, smartphones, firewalls, routers, copiers, scanners, printers, memory cards, cameras, and flash drives have in common? They all store data that should be permanently removed before handing down, recycling, or discarding.
The data can be apparent, hidden, temporary, cached, browser-based, or metadata:
Apparent data files are files that authorized users can view and access.
Hidden files are files that the operating system by design does not display.
Temporary files are created to hold information temporarily while a file is being created.
A web cache is the temporary storage of web documents, such as HTML pages, images, and downloads.
A data cache is the temporary storage of data that has recently been read and, in some cases, adjacent data areas that are likely to be accessed next.
Browser-based data includes the following items:
Browsing history, which is the list of sites visited
Download history, which is the list of files downloaded
Form history, which includes the items entered into web page forms
Search bar history, which includes items entered into the search engines
Cookies, which store information about websites visited, such as site preferences and login status
Metadata is details about a file that describes or identifies it, such as title, author name, subject, and keywords that identify the document’s topic or contents.
Removing Data from Drives
A common misconception is that deleting a file will permanently remove its data. Deleting (or trashing) a file removes the operating system pointer to the file. Formatting a disk erases the operating system address tables. In both cases, the files still reside on the hard drive, and system recovery software can be used to restore the data. To give you an idea of how easy it is to recover information from a formatted hard drive, simply Google the phrase “data recovery” and see what comes back to you. Utilities are available for less than $50 that are quite capable of recovering data from formatted drives. Even if a drive has been formatted and a new operating system installed, the data is recoverable.
NIST Special Publication 800-88 Revision 1 defines data destruction as “the result of actions taken to ensure that media cannot be reused as originally intended and that information is virtually impossible to recover or prohibitively expensive.” There are two methods of permanently removing data from a drive—disk wiping (also known as scrubbing) and degaussing. The disk wiping process will overwrite the master boot record (MBR), partition table, and every sector of the hard drive with the numerals 0 and 1 several times. Then the drive is formatted. The more times the disk is overwritten and formatted, the more secure the disk wipe is. The government medium security standard (DoD 5220.22-M) specifies three iterations to completely overwrite a hard drive six times. Each iteration makes two write passes over the entire drive; the first pass inscribes ones (1) over the drive surface and the second inscribes zeros (0) onto the surface. After the third iteration, a government-designated code of 246 is written across the drive, and then it is verified by a final pass that uses a read-verify process. There are several commercially available applications that follow this standard. Disk wiping does not work reliably on solid-state drives, USB thumb drives, compact flash, and MMC/SD cards.
Degaussing is the process wherein a magnetic object, such as a computer tape, hard disk drive, or CRT monitor, is exposed to a magnetic field of greater, fluctuating intensity. As applied to magnetic media, such as video, audio, computer tape, or hard drives, the movement of magnetic media through the degaussing field realigns the particles, resetting the magnetic field of the media to a near-zero state, in effect erasing all the data previously written to the tape or hard drive. In many instances, degaussing resets the media to a like-new state so that it can be reused and recycled. In some instances, this simply wipes the media in preparation for safe and secure disposal. The National Security Agency (NSA) approves powerful degaussers that meet their specific standards and that in many cases utilize the latest technology for top-secret erasure levels.
Cryptographic Erase is a technique that uses the encryption of target data by enabling sanitization of the target data’s encryption key. This is done to leave only the cipher text on the media and preventing read-access, because no one should have the encryption key. It is common for storage manufacturers to include integrated encryption and access control capabilities, also known as self-encrypting drives (SEDs). SEDs feature always-on encryption that ensures that all data in the storage device is encrypted. In practice, cryptographic erase can be executed in a fraction of a second. This is a great benefit because nowadays other sanitization methods take more time in large storage devices. Cryptographic erase can also be used in addition to other data destruction methods. You should not use cryptographic erase to sanitize data if the encryption was enabled after sensitive data was stored on the device without having been sanitized first. In addition, you should not use cryptographic erase if you are not certain if sensitive data was stored on the device without being sanitized prior to encryption.
Destroying Materials
The objective of physical destruction is to render the device and/or the media unreadable and unusable. Devices and media can be crushed, shredded, or, in the case of hard drives, drilled in several locations perpendicular to the platters and penetrating clear through from top to bottom.
Cross-cut shredding technology, which reduces material to fine, confetti-like pieces, can be used on all media, ranging from paper to hard drives.
It is common for organizations to outsource the destruction process. Companies that offer destruction services often have specialized equipment and are cognizant of environmental and regulatory requirements. The downside is that the organization is transferring responsibility for protecting information. The media may be transported to off-site locations. The data is being handled by non-employees over whom the originating organization has no control. Selecting a destruction service is serious business, and thorough due diligence is in order.
Both in-house and outsourced destruction procedures should require that an unbroken predestruction chain of custody be maintained and documented and that an itemized post-destruction certificate of destruction be issued that serves as evidence of destruction in the event of a privacy violation, complaint, or audit. NIST Special Publication 800-88 Revision 1 mentions that destructive techniques also render a “device purged when effectively applied to the appropriate media type, including incineration, shredding, disintegrating, degaussing, and pulverizing.”
Stop, Thief!
According to the Federal Bureau of Investigation (FBI), on average, a laptop is stolen every 53 seconds, and one in ten individuals will have their laptop stolen at some point. The recovery statistics of stolen laptops is even worse, with only 3% ever being recovered. This means 97% of laptops stolen will never be returned to their rightful owners. The Ponemon Institute has conducted several studies and reported that almost half of laptops were lost or stolen off-site (working from a home office or hotel room) and one third were lost or stolen in travel or transit. The statistics for mobile phones and tablets is even worse.
The cost of lost and stolen devices is significant. The most obvious loss is the device itself. The cost of the device pales in comparison to the cost of detection, investigation, notification, after-the-fact response, and economic impact of lost customer trust and confidence, especially if the device contained legally protected information. The Ponemon Institute “2017 Cost of Data Breach Study: Global Overview” (https://www-01.ibm.com/common/ssi/cgi-bin/ssialias?htmlfid=SEL03130WWEN) calculated the average business cost of a breach in the United States to be $141 per record across all industries.
Consider this scenario: A laptop valued at $1,500 is stolen. A file on the laptop has information about 2,000 individuals. Using the Ponemon conclusion of $141 per record, the cost of the compromise would be $282,000! That cost doesn’t include potential litigation or fines.
Additional examples of things that are attractive to thieves are modern portable media theft, such as thumb or pen drives and SD cards. This is why it is important that you have a good asset inventory. In Chapter 5, “Asset Management and Data Loss Prevention,” you learned that asset management is crucial. In addition, you learned that every information asset must be assigned an owner. The success of an information security program is directly related to the defined relationship between the data owner and the information. In the best-case scenario, the data owner also functions as a security champion enthusiastically embracing the goals of confidentiality, integrity, and availability (CIA).
You should also have an established and effective process for individuals to report lost or stolen devices. Additionally, you should have mitigations in place in case of theft. These mitigations include encryption and remote wipe capabilities for mobile devices. Typically, remote wipe is a function of a mobile device management (MDM) application.

